Secure Software Development Lifecycle
Security is especially important part of any application that covers critical functionality. It can be as simple as securing your database or customers data from the attackers. In this blog we will see how the SDLC works and how we can make it secure.
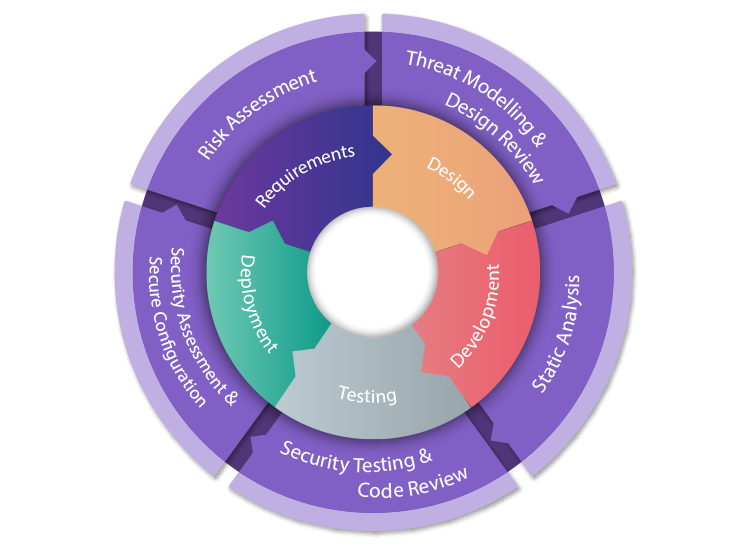
Most of the companies still follow the traditional Software Development Lifecycle (SDLC) where they cover security after completing the development or deployment and this is not a good practice for developing a secure application this could impact the overall application when the application goes live. When companies follow strictly to the traditional Software Development Life Cycle (SDLC), security often is not given primary consideration. This is because during the planning phase, there might arise scenarios where potential vulnerabilities or loopholes could compromise customer data. It is important to thoroughly address every scenario across various phases of development. For instance, during the requirement gathering phase for an application, it is crucial to actively seek out security concerns alongside other requisites. This practice extends throughout multiple phases, ensuring that security considerations are systematically integrated at each stage of the development process.
Understanding SDLC
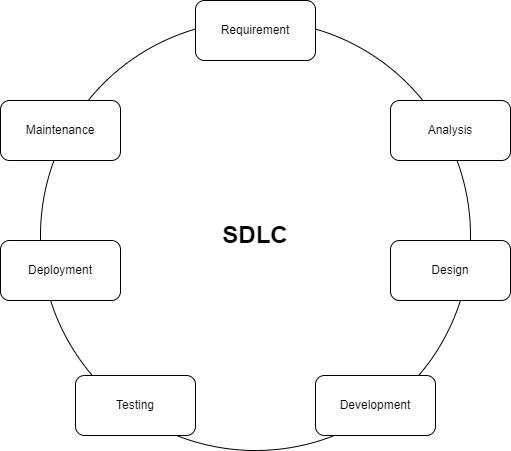
Software Development Lifecycle refers to a methodology with clearly identified the process for creating high-quality software. It usually involves of following phases:
• Requirement gathering
• Analysis of the requirements to guide design
• Design of new features based on the requirements
• Testing and verification of new capabilities
• Deployment of the features
• Maintenance and evolution of these capabilities once the release goes out the door
SDLC or Software Development Life Cycle is a process that produces software with highest quality at lowest cost in the shortest time possible. SDLC provides a well-structured flow of phases which helps an organization to quickly produce high quality software which is well-tested and ready for production use.
How SDLC Work’s?
SDLC works by lowering the cost of software development while simultaneously improving the quality and shortening production time. SDLC give us a plan by following the plan we can remove the typical pitfalls of software development projects. That plan starts by evaluating existing systems faults.
Next, it defines the requirements of the new system. It then creates the software through the stages of analysis, planning, design, development, testing and deployment. By anticipating costly mistakes like failing to ask the end user or client for feedback. SDLC can eliminate redundant rework and after-the-fact fixes.
It is also important to know that there is a strong focus on the testing phase. As the SDLC is repetitive methodology, you must ensure the quality at every cycle. Many organizations tend to spend few efforts on testing while a stronger focus on testing can save them a lot of rework, time, and money. Be smart and write the right types of tests.
Now, Let's explore the various stages of the Software Development Life Cycle.
Following are the best practices or stages of the SDLC ensures the process works in a smooth, efficient, and productive way.
1. Requirement Gathering: This stage of the SDLC means gaining input from all investors, including customers, salespeople, industry experts, and programmers. Learn the strengths and weaknesses of the current system with improvement as the goal.
2. Analysis: Continuous collaboration using Git and GitHub
3. Design: This phase of the SDLC starts by turning the software specifications into a design plan called the Design Specification. All stakeholders then review this plan and offer feedback and suggestions. It is crucial to have a plan for collecting and incorporating stakeholder input into this document. Failure at this stage will certainly result in cost overruns at best and the total collapse of the project at worst.
4. Development: At this stage, the actual development starts. It is important that every developer sticks to the agreed blueprint. Also, make sure you have proper guidelines in place about the code style and practices. For example, define a nomenclature for files or define a variable naming style such as camelCase. This will help your team to produce organized and consistent code that is easier to understand but also to test during the next phase.
5. Testing: In this stage, we test for defects and deficiencies. We fix those issues until the product meets the original specifications. In short, we want to verify if the code meets the defined requirements.
6. Deployment: At this stage, the goal is to deploy the software to the production environment so users can start using the product. However, many organizations choose to move the product through different deployment environments such as a testing or staging environment. This allows any stakeholders to safely play with the product before releasing it to the market. Besides, this allows any final mistakes to be caught before releasing the product.
7. Maintenance: Software Maintenance refers to the process of modifying and updating a software system after it has been delivered to the customer. This can include fixing bugs, adding new features, improving performance, or updating the software to work with new hardware or software systems. The goal of software maintenance is to keep the software system working correctly, efficiently, and securely, and to ensure that it continues to meet the needs of the users.
Understanding Secure SDLC
Secure SDLC says “Security is not a milestone or phase, it’s a process which you have to apply at every phase in Software Development Lifecycle” unlike traditional software development and it needs to be forefront of your developer’s mind. Security issues can be addressed in the SDLC pipeline well before deployment to production with the help of dedicated efforts and the right security solutions. Secure SDLC address security at every step of the Software Development Life Cycle.
Why is Secure SDLC Important?
The days of releasing a product into the wild and addressing the bugs in subsequent patches are gone. Now Developers need to be familiar of potential security vulnerabilities at each step of the process. In Secure SDLC process you think like an attacker and able to understand the possible attacks which can harm your application. So, when you find the vulnerabilities at each phase of SDLC at the end you will not get the big crash in your application. This reduces the risk of finding security vulnerabilities in your app and works to minimize the impact when they are found. Implementing SDLC security affects every phase of the software development process.
How does SDLC address security?
Security is an essential aspect of any software development process. However, unlike traditional software development that addresses security as a separate stage, SDLC addresses security every step of the way through DevSecOps practices. DevSecOps, an extension of DevOps, is a methodology that emphasizes the integration of security assessments throughout the entire SDLC. It ensures that the software is secure from initial design to final delivery and can withstand any potential threat. During DevSecOps, the team undergoes security assurance activities such as code review, architecture analysis, penetration testing, and automated detection, which are integrated into IDEs, code repositories, and build servers.
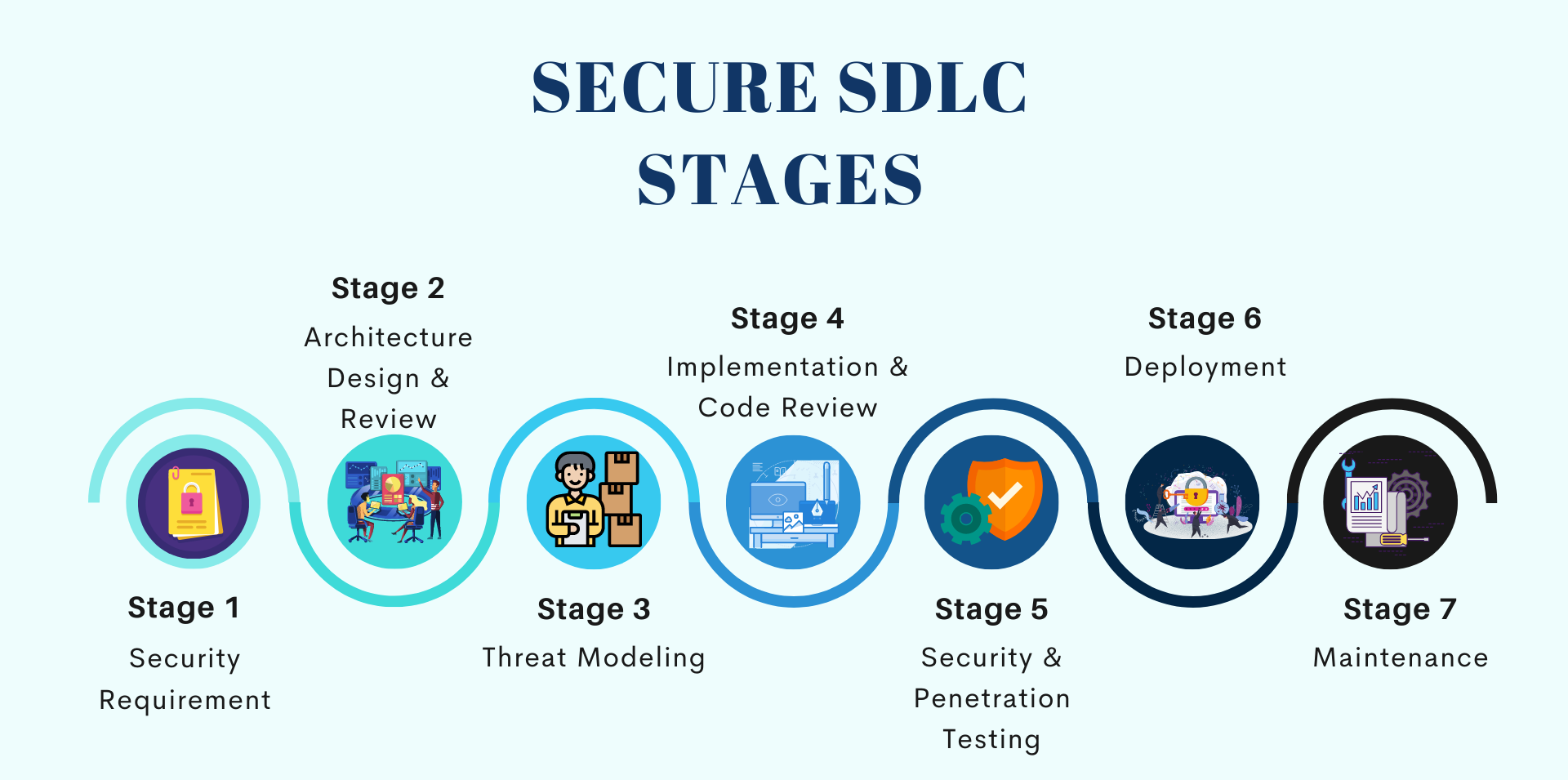
How can DevSecOps be integrated into SDLC?
By following some best practices, DevSecOps can be integrated into SDLC in many ways.
• Planning and Requirement Analysis: Here, security requirements and appropriate security choices that can mitigate potential threats and vulnerabilities are identified in this stage. What security design principles and best practices to be used are also thought about here.
• Architectural Design: The development team uses the security design principle and architecture to consider potential risks. This stage involves threat modelling, access control, encryption mechanism, and architecture risk analysis.
• Software Development and Testing: The code reviews are done to ensure software follows code standards and security controls are implemented. Security vulnerability tests like penetration testing are also done to identify potential issues.
• Deployment: Automated DevSecOps tools are used to improve application security. To ensure the software is deployed securely, firewalls, access controls, and security settings are configured.
• Maintenance: Security continues after deployment. The team must continuously monitor the software for security vulnerabilities. The team would also update the software with security patches and updates, as necessary.
Security Best Practices keep in mind while doing Software Development:
• Using parameterized, read-only SQL queries to read data from the database and minimize chances that anyone can ever grab these queries for evil purposes.
• Validating user inputs before processing data contained in them.
• Sanitizing any data that is being sent back out to the user from the database.
• Checking open-source libraries for vulnerabilities before using them.
• Always Store and pass customers sensitive data in encrypted format like PII Details.
• Use strong and fast Encryption for sensitive data because data should be processed securely and faster both.
• Use automation tools for testing application security like checkmarx etc.
• Do not hardcode the secret keys in your code because your code visible to the end users in the bundle.
Use Case
Failure to address security at every stage of the Software Development Life Cycle (SDLC) can lead to numerous vulnerabilities, potentially resulting in the compromise of both the application and its associated data. Several common vulnerabilities frequently occur if security is not effectively considered:
• Broken Access Control: Broken Access Control happens when access permissions are misconfigured thereby allowing attackers to access, modify or delete data, files, and accounts that they should not have access to in the first place.
• Cryptographic Failures: Cryptographic failures occur when sensitive data is insufficiently protected and therefore leaked or exposed to unauthorized audiences. Such failures are most common if data is transmitted or stored in clear text or using known-to-be-weak cryptographic algorithms such as MD5 or SHA-1.
• Injection: An attacker can execute unintended commands or gain access to sensitive data by injecting malicious data as part of a command or query. This usually happens when a website fails to filter, validate or sanitize users’ inputs or implement parameterization.
• Insecure Design: It is different from insecure implementation in that it has more to do with risks related to design and architectural flaws. A secure implementation might have an insecure design which still renders a web application vulnerable to attacks and exploits.
• Security Misconfiguration: This category covers a brand range of potential vulnerabilities including insecure default configurations, incomplete configurations, and misconfigured HTTP headers, using insecure default usernames and passwords, etc.
• Vulnerable and Outdated Configuration: This refers to known issues where vulnerabilities exist because developers either do not know the versions of components used including those of nested dependencies, or are not aware that the software used is already unsupported or out of date.
• Server-Side Request Forgery: Server-Side Request Forgery (SSRF) occurs when a web application proceeds to fetch data without first validating user-supplied URL. In a bid to provide end-users with convenience, fetching data using a URL has become more common. The vulnerability allows an attacker to compel the web application to send a crafted request to unexpected destinations even when adequately protected by firewalls, VPNs and Network Access Control List (ACL).
We can mitigate most of the vulnerabilities by following the Secure SDLC.
In the development of an application or feature, our process consists of several key steps: Requirement Analysis, Architectural Design, Software Development, Software Testing, Deployment, and Maintenance. Each step plays a critical role, and by diving into them individually, we gain a complete understanding of the entire process.
• Requirement Analysis
Description: Within this stage, we undertake two sub-steps: sprint planning and sprint grooming. During sprint planning, all stakeholders convene to discuss a problem statement. We delve into understanding the problem, gathering requirements, identifying security concerns, defining user flows, and anticipating challenges. This terminates in a thorough plan detailing what needs development and how to proceed. Subsequently, in the sprint grooming session, stakeholders reconvene to refine the plan and pinpoint any gaps. This collaborative meeting involves gathering feedback, addressing challenges, and engaging in detailed discussions to fine-tune approaches and plans, ensuring thorough gap identification.
We create essential documents like SRS (Software Requirements Specification) or Technical Documents, leveraging tools such as Confluence for secure document creation and sharing. Meanwhile, Jira serves as our task and ticket tracking tool, facilitating full control of the project. It aids in understanding the scope of work, monitoring task progress, and effectively managing the project.
Tools Used: Confluence, Jira, Zoho, Click Up
• Architectural Design
Description: During this stage, we craft the visual layout and functionality of our application, ensuring a user-friendly and interactive experience. Utilizing Figma, we design components and screens that prioritize ease of use and ability while considering robust security principles and architecture to mitigate potential risks. For instance, in developing a feature for updating user passwords, we integrate a two-factor authentication mechanism to strengthen password updates and enhance overall security.
Tool Used: Figma, Adobe XD, Sketch, In Vision
• Software Development
Description: This stage holds great consequence within the software development lifecycle. Here, we initiate development by creating reusable components, placing a paramount emphasis on security. We prioritize coding best practices, leveraging extensions like Sonar Lint to swiftly identify any coding issues. Safeguarding private keys stands as a pivotal aspect of this phase; thus, we securely store these keys in an ansible vault on our servers. Encryption plays a crucial role in processing and transferring sensitive information, such as PII (Personally Identifiable Information), across networks, ensuring both swift encryption and decryption processes to expedite response times. We write test cases concurrently during development to ensure that our code operates as expected and to promptly identify any potential defects or inconsistencies.
Additionally, we invest in developer training and collaborative sessions to enhance security awareness and identify potential concerns. Throughout development, we adhere to the three fundamental principles of information security: confidentiality, integrity, and availability. These principles serve as guiding pillars, ensuring a robust security structure as we increase through the development phase.
Confidentiality: Confidentiality measures are designed to prevent unauthorized disclosure of information. The purpose of the confidentiality principle is to keep personal information private and to ensure that it is visible and accessible only to those individuals who own it or need it to perform their organizational functions.
Integrity: Consistency includes protection against unauthorized changes (additions, deletions, alterations, etc.) to data. The principle of integrity ensures that data is accurate and reliable and is not modified incorrectly, whether accidentally or maliciously.
Availability: Availability is the protection of a system’s ability to make software systems and data fully available when a user needs it (or at a specified time).
Tools Used: Sonar Lint, TS Lint
• Software Testing
Description: Upon completing the development phase, we conduct a comprehensive code scan utilizing the SonarQube Tool, aiming to pinpoint areas of shabby code, code smells, and potential vulnerabilities. Subsequently, we address these issues during the testing stage. Following the resolution of SonarQube-identified problems, we proceed with manual testing in a local environment, ensuring the functionality aligns with expectations. Additionally, we engage in security vulnerability testing, such as penetration testing, to proactively identify and mitigate potential security risks.
Tools Used: SonarQube, Checkmarx, Kiuwan
• Deployment
Description: During this phase, our objective is to deploy the software into the production environment for user access, yet we opt to transition it through various deployment environments like testing or staging. This approach grants us a safe space to evaluate the product before its market release, allowing any final errors to be identified and rectified. To automate our deployment process, we utilize Jenkins. When releasing the product into the testing environment, we've established a deployment protocol that involves using Checkmarx, an automation tool, to identify potential security vulnerabilities. Checkmarx conducts an automatic scan of our application during deployment, enabling us to enhance its security before delivering a highly secure application to end-users.
Additionally, as part of the deployment process, the test cases authored during development are automatically executed within Jenkins. If any test case fails, the deployment is halted, prompting us to rectify and retest the failed cases before redeploying the application. This meticulous testing regimen ensures the reliability and functionality of the deployed software.
Tool Used: Jenkins, Checkmarx.
• Maintenance
Description: Following the deployment of the application across testing and production environments, our ongoing practice involves continuous monitoring to detect security vulnerabilities. This entails manual testing to meticulously identify any potential risks or vulnerabilities. Additionally, we remain proactive in updating the software with necessary security patches and updates to ensure its resilience against emerging threats.
This precise process we follow to develop and deliver a highly secure and robust application to the end users.
Conclusion
In today's digital age, where technology is pivotal for business success, security stands as one of the most crucial aspects of software development. Customers place their trust in our products and processes with the expectation that we will safeguard their data from malicious intent. It is imperative that if we make assurances to our customers regarding data security, we should diligently fulfil those commitments. Upholding this promise is foundational to business success; by fostering a relationship of trust with our customers, we assume the responsibility of safeguarding their sensitive information, thereby ensuring the permanency and success of our enterprise. Secure SDLC empowers your teams to work more collaboratively, release higher-quality and secured software, and respond swiftly to the ever-changing demands of the market. The importance of Secure SDLC cannot be overstated – it is the path to staying ahead in the rapidly evolving world of technology.
I hope you loved this article. Stay Happy!