How to Implement Secure and Fast Encryption
Organizations have few essential tools at their clearance to ensure strong cybersecurity which includes encryption, authentication, and authorization. Encryption is one of the most beneficial, first-level coats to protecting your data and staying cyber strong.

In this blog, you’ll learn about what it is and what occurs when you encrypt your data. You’ll also understand how end-to-end data encryption helps to avoid data breaches so you can better defend your business from cyberattacks.
What is Encryption?
Encryption is the procedure through which data is encoded so that it continues to be hidden from or inaccessible to unauthorized users. It helps protect private information, sensitive data, and can enhance the security of interaction between client apps and servers. In real meaning, when your data is encrypted, even if an unauthorized person or entity gets access to it, they will not be able to read it.
How to encrypt data
The procedure itself is straightforward: an encryption key uses an algorithm to translate (encode) plaintext or readable data into unreadable data or ciphertext. Only the corresponding decryption key can decode the jumbled ciphertext back into readable plaintext.
Types of Encryption Systems
There are many different types of encryption algorithms and methods to pick from, so how do you know which one is the securest choice for your cybersecurity essentials? Let’s begin with the most common types of encryption systems: symmetric vs asymmetric encryption.
Symmetric Encryption
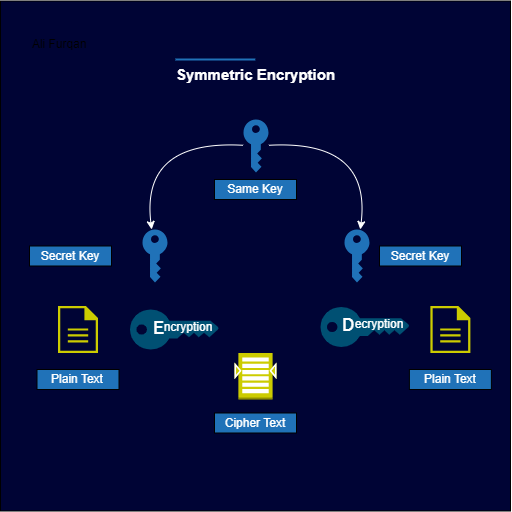
Symmetric encryption relies on a single key for both encryption and decryption, necessitating the use of the same key for both processes. These algorithms excel in bulk data encryption, offering speed and straightforward implementation through hardware. However, a drawback lies in the fact that anyone possessing the decryption key can decrypt the data, even if they're not the intended recipient.
Asymmetric Encryption
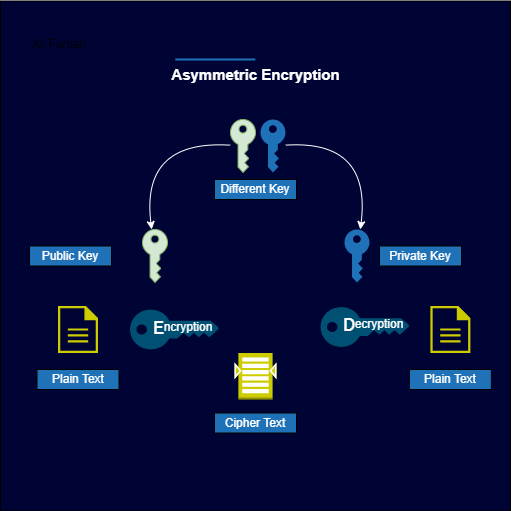
Asymmetric encryption involves the use of two distinct keys: a public key, responsible for encrypting sensitive information or data, and a private key, responsible for decrypting the encrypted data. The public key can be freely distributed, allowing others to encrypt data that only the possessor of the corresponding private key can decrypt. This private key must be kept confidential to ensure the security of communication or information exchange.
A collection of algorithms exists for both symmetric and asymmetric encryption, offering choices based on specific use cases. AES (Advanced Encryption Standard) serves as an established symmetric encryption method, while RSA (Rivest, Shamir, and Adleman) stands as a widely adopted asymmetric encryption technique within the IT industry. So, as we know that the AES Encryption is faster but not very secure and RSA Encryption is secure but not much faster. To achieve a secure and efficient encryption method for sensitive data transmission, a hybrid approach combining symmetric and asymmetric encryption is necessary. While symmetric encryption, like AES, uses a single key for both encryption and decryption, it poses a risk if the key is compromised. On the other hand, asymmetric encryption, such as RSA, utilizes a pair of keys (public and private) for encryption and decryption, providing enhanced security but often with slower processing and size limitations.
Combining Symmetric and Asymmetric Encryption
The proposed solution involves leveraging both encryption methods harmoniously. Asymmetric encryption can be used to securely exchange a symmetric key between the client and server. Once the symmetric key is established, it enables faster encryption and decryption of the bulk data while maintaining the security offered by the asymmetric encryption's key exchange mechanism. This combined approach ensures both strong security and optimal performance for handling sensitive information in bank applications. In this type of encryption individual symmetric keys would be generated for each session and exchange those keys securely with the help of Asymmetric encryption just like the TLS Handshake process.
TLS/SSL Handshake
A Secure Sockets Layer (SSL) / Transport Layer Security (TLS) handshake is the procedure of creating a safe and secure encrypted communication channel between the client (user’s browser) and the server (web server). Hence, protecting user information and ensuring risk-free transactions by preventing an attacker from reading or changing the actual data.
What happens during a TLS/SSL Handshake Process
There are few steps which need to be complete TLS/SSL Handshake depend on the encryption algorithm used, but the essential process is as follows:
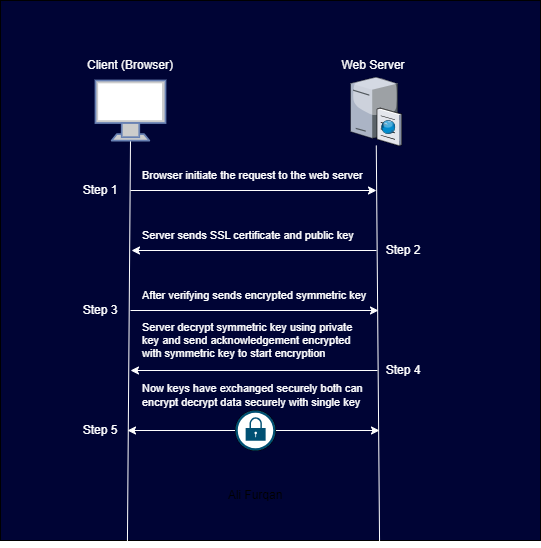
Step 1: Browser initiates a request to the web server to access an application or website.
Step 2: Server transmits an SSL certificate containing its public key, utilized for encrypting data. Within its infrastructure, the web server holds both a public and a private key. The server shares the public key with end-users for encryption purposes while protecting the private key securely within its restrictions, as it remains inaccessible and undisclosed to external entities.
Step 3: Upon receiving the SSL certificate and public key, the browser conducts several validations: it verifies the certificate's root against a catalog of trusted CAs (Certificate Authorities), ensures the certificate's validity by confirming it's unexpired and unrevoked, and checks that its common name aligns with the connected website. If the certificate gains the browser's trust, it initiates the creation of a symmetric key. This key is encrypted using the web server's received public key. Subsequently, the browser transmits the encrypted symmetric session key back to the web server, facilitating the exchange and establishment of a secure communication channel.
Step 4: Server receives encrypted symmetric key and decrypts the key with the help of private key which stores in the web server.
Step 5: With the successful and secure exchange of keys, both the client and server are now capable of encrypting and decrypting bulk data, enabling secure and efficient communication between them.
Conclusion
So, by utilizing a combination of symmetric and asymmetric encryption, you can implement a robust and convenient encryption method, ensuring both secure transmission and fast encryption and decryption of bulk data.
I hope you liked this informational article and have learnt something new. Stay Happy!